- WORM Storage Introduction
Write Once Read Many (WORM) describes a data storage device in which information, once written, cannot be deleted or modified. This write protection affords the assurance that the data cannot be tampered with once it is written to the device. The CD-R and DVD-R optical discs for computers are common WORM devices. Due to the limitations of capacity and performance, optical discs have limitations in efficiently archiving and utilizing large amounts of data . So, multiple vendors beginning in the mid 2000s developed Magnetic WORM devices. These archival grade storage devices utilize a variation of RAID and magnetic storage technologies to secure data from unauthorized alteration or modification at both the hardware and software levels.
Company Overview and Product Introduction (.pdf)
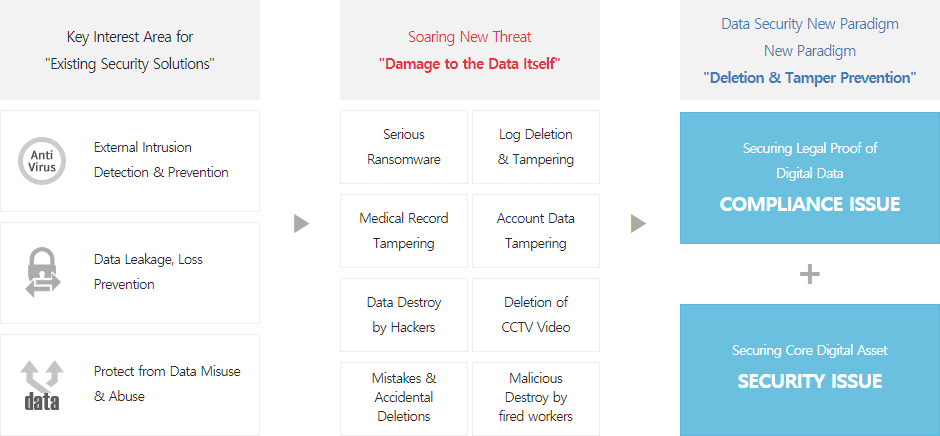
Businesses are required to keep data for regulatory, compliance, or legal reasons. Despite backup retention policies built into many legacy backup software packages, administrators often have the ability to inadvertently delete or modify data governed by higher-level business requirements, either by changing policy in the backup software or potentially bypassing the backup software and accessing the underlying storage directly.
As the value of data and the need to retain it grows, businesses often want to protect data beyond just setting retention times. In addition to the inherent value of data, regulatory bodies in many industries have stringent data retention requirements which can be costly if not met.
Businesses therefore need an additional enforcement on retention such that people with administrative privileges cannot alter this data. The technology requirement for maintaining read-only access without deletion or modification over a specified period is written into many regulations and internal policies.
It is the age when most of the data is digitally created, stored and utilized. Most of the organization's core data and digital assets are exposed to malicious software including ransomware, hacking and various forms of intentional deletion and tampering. Once stored on WORM storage, the data is absolutely secure from these various threats. Therefore, various solutions, such as backup and document management, tend to store critical data on WORM storage for more secure data archiving.
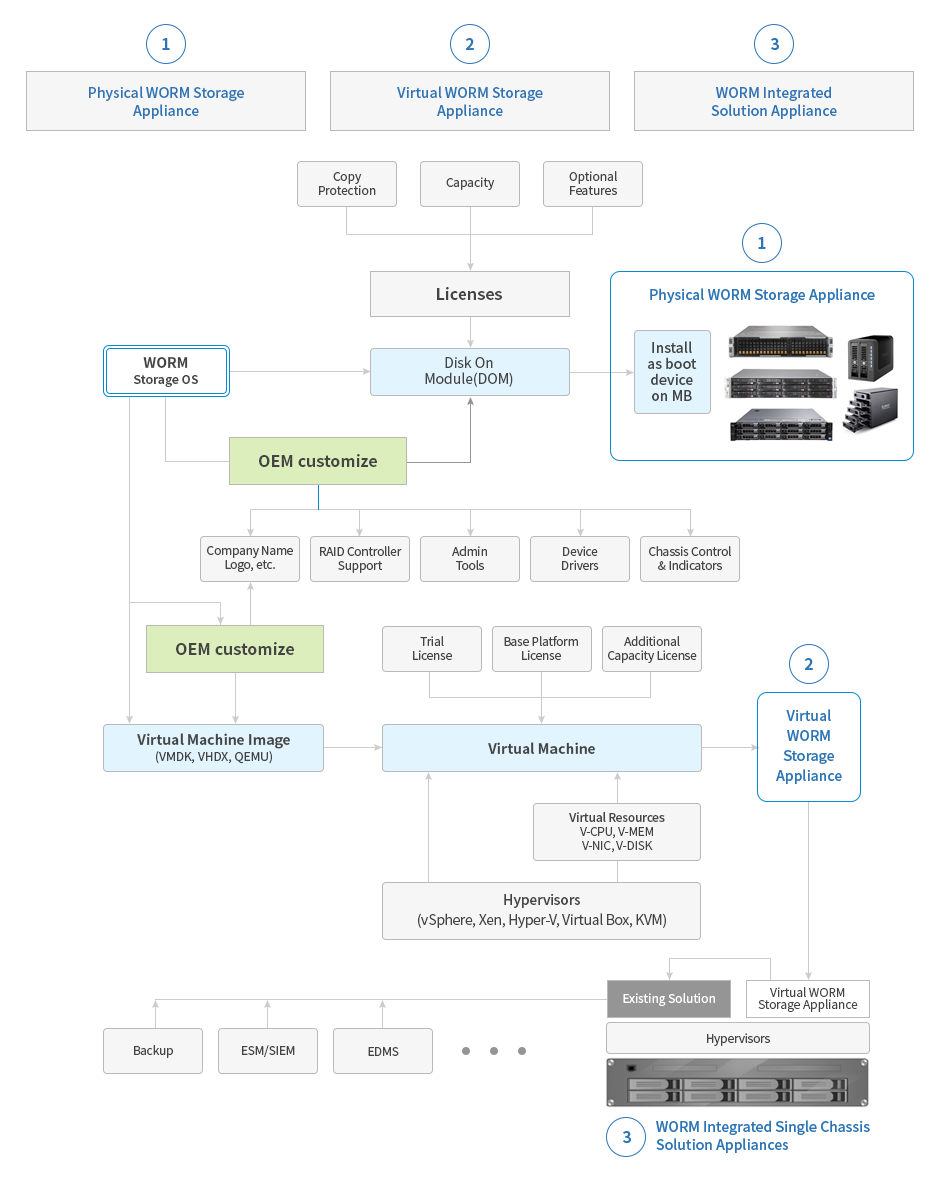
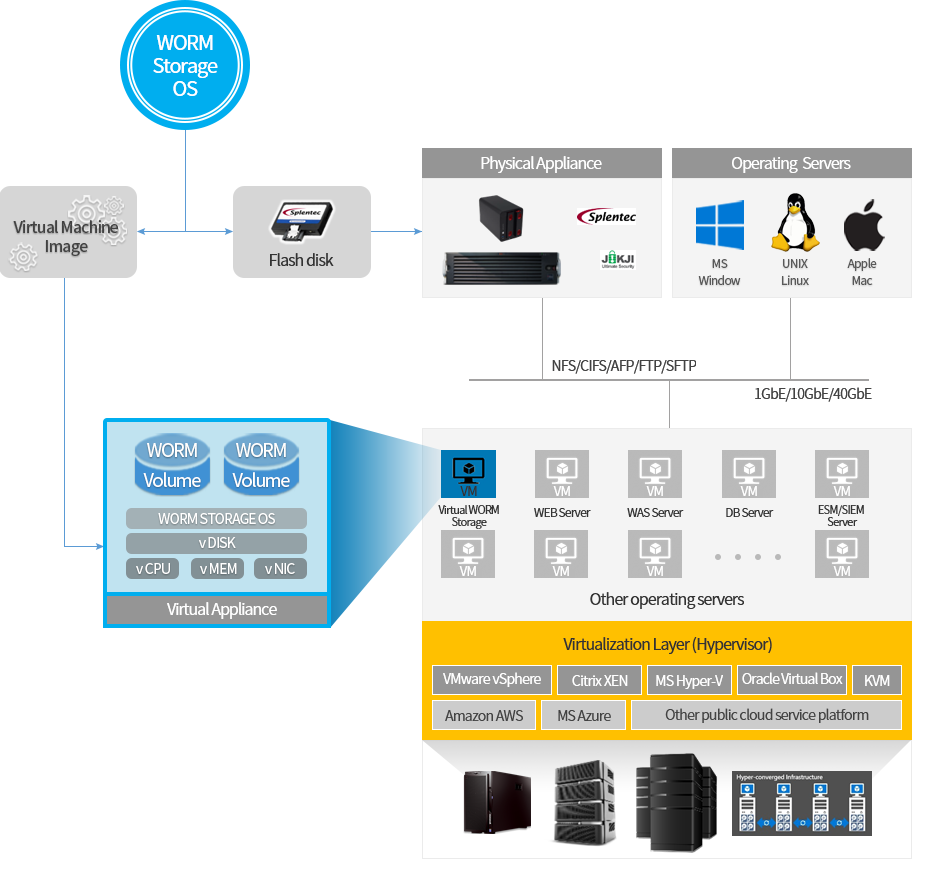
Olivetech has core technologies for WORM storage OS based on Embedded Linux that drives large capacity, high performance WORM storage systems based on hard disk or SSD. When the Olivetech WORM storage OS is installed in the DOM(Disk On Module, a kind of stable flash memory disk) with SATA, USB, M.2 interfaces and installed as a boot device on an Intel X-86 based server system, the system becomes a physical WORM storage appliance. The WORM storage OS can also be installed in a virtual machine and used as a virtual WORM storage appliance. OliveTech offers a wide range of physical WORM storage appliance products and virtual WORM storage appliances that can take advantage of WORM storage capabilities across a variety of virtualization platforms through the purchase of software licenses and capacity licenses. In addition, OliveTech can license WORM storage OS to enable each company to develop and manufacture its own WORM storage model and also can provide some level of customization under proper condition.
Data protection is implemented in a hard-coding fashion inside the WORM storage OS kernel. It is therefore not possible to avoid protection by removing or bypassing the function.
It does not provide any special permissions or tools to delete or change the data once saved, and even the manufacturer does not implement or maintain these tools.
Files that are stored on a WORM volume are assigned a retention period. During the specified retention period, it can not be deleted by any authority including super user. Changing the retention period during the retention period is not allowed. Files whose retention period has expired are allowed to be deleted and the retention period can be extended further. Even if the retention period has expired, modification is not allowed to guarantee originality. Unless otherwise specified, the retention period for files is automatically assigned the volume default retention period specified in the volume in minutes, hours, days, weeks, years units and permanent. An additional step is available to assign a file a different retention period than the volume default.
Files stored on a WORM volume are finally committed through a commit command to a file with a non-erasable, non-rewritable attribute. This is called a “trigger” command. Any file on a WORM volume can be deleted and modified before the trigger. If you select "Auto-Trigger" among the volume attributes, the file will automatically have the WORM attribute when you save it, even if there is no separate trigger command.
It is possible to protect the data recorded in the file from being modified at the moment of recording even before triggering. To protect files in this way, you can create a file with a special WORM file attribute called Append-Only mode. Files created with this attribute can not be deleted, data is only allowed to be appended to the end of the file, and modification of previously recorded portions is not allowed. This property is useful for real-time log retention and so on.
To prevent neutralizing the retention period by changing the system time, it can be chosen to operate a independent software time mechanism for managing retention period on a volume-by-volume basis.
A digital fingerprint based on the SHA256 hash function can be created and saved for each file. This value is used later to verify the integrity of the file.
When data is stored on a WORM volume, it can be encrypted and recorded in real time. The encryption key can be stored inside the system so that the encrypted volume can be automatically mounted at system start-up, or an administrator can manually enter the password to mount the encrypted volume every time the system is started.
Provides the ability to find changed files on the source volume and periodically synchronize them to the target volume. The target volume can be on the same system or on a different system and the WORM file attributes of a file, including the retention period, remain the same on the replica.
It provides real-time, block-by-block replication of two volumes between WORM storage systems. The WORM file properties, including the retention period, remain the same on the replica.
Record the history of various activities that connect and access WORM storage for audit purposes. This log ensures the integrity of the record by making it impossible to delete and tamper by any authority.
WORM storage is accessed through industry standard interfaces such as NFS, CIFS, FTP, and SFTP, as well as standard NAS. Commands for handling WORM file attributes such as trigger and retention period are also provided through POSIX standard commands and APIs.
A WORM storage system can be configured with one of two levels of security. In both levels, deletion and modification of files are not allowed, even for WORM storage administrator. The difference between the two levels is that in flexible security mode, the storage administrator has an interface to delete WORM volumes, and in strict security mode, WORM storage administrators do not have the right to delete WORM volumes. Flexible security mode can be upgraded to strict security mode only once, while downgrade to flexible security mode is not allowed.
WORM volumes, generic NAS volumes, and iSCSI volumes can be created and operated on one storage system at the same time.
Most of the functions provided by common NAS are provided, including network management, volume management, account management, quota management, and share management.
All system management is done through the management tools provided through a web browser.
VMware vSphere, Citrix Xen, Microsoft Hyper-V, Oracle VirtualBox, KVM and KVM derivatives
VMDK, VHDX, QEMU
| Trial License | · 30 Day Free-Trial License |
|---|---|
| Base Platform License |
· WORM volume can be created up to 2TB in total · To configure a WORM volume more than 2TB, Additional Capacity License is required |
| Additional Capacity License | · Licenses for additional configurations of WORM volumes that can be purchased in 1TB unit |